Easily Deploy Derived Credentials with Microsoft InTune™
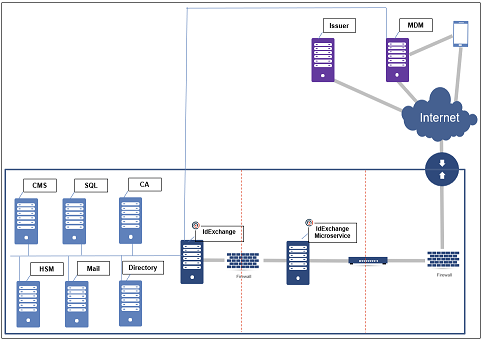
IdExchange™ adds custom PKI, device verification, and issuance rules to augment InTune’s certificate distribution capabilities to enable greater controls during the issuance process, auditing, and deployment flexibility for organizations. With IdExchange, organizations can rapidly deploy certificates to mobile devices without additional mobile software or changes to their existing PKI infrastructure.
Features
- Enforce custom issuance rules, including NIST derived credential security processes, for mobile certificate issuance
- Use your existing, internal CA without having to install NDES or opening your Firewall
- No additional mobile software required – just the Intune company portal
- Extensive for certificates issued, InTune SCEP processing, and expiring certificates
Requirements
- Microsoft InTune
- CyberArmed IdExchange
- Certificate Authority (Microsoft CA, IdenTrust, Entrust, Comodo/Sectigo)
- PIV/CIV credential
The types of organizations that would benefit
- Organizations that have already issued smart cards with the HID CMS and now want to extend PKI credentials to mobile devices.
- Organizations with InTune that want to distribute certificates but do not change their existing PKI infrastructure.
- Organizations desiring additional identity and device proofing capabilities for their mobile certificate distribution process.
How it works
IdExchange™ drastically simplifies the issuance of PKI credentials by seamlessly linking different identity proofing, credential issuance, and certificate authority systems into a single platform. Once installed, organizations have the ability to implement custom issuance rules, link existing badging system, and issue PKI certificates from their own certificate authority.
Read our blog to learn more about how we enhanced the InTune certificate distribution capability.
Link IdExchange and InTune
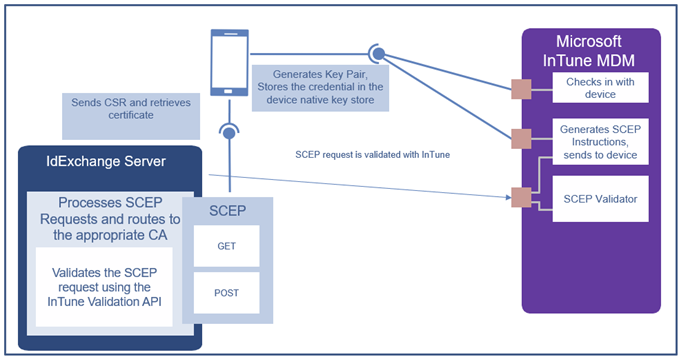
Install IdExchange in your infrastructure and then connect to InTune using the secure API registration process. Once connected, IdExchange will be able to retrieve the devices assigned to the users to help automate the registration process.
User submits request
The user authenticates with their existing smart card credential to request the derived credential. This action allows the operator to properly verify the end user using their existing PKI credential, thus eliminating the need for a separate verification process.
Issuance officer approval
Once the request has been submitted, a separate individual will review the request and approve it. This second individual enforces multi-person control which ensures certificates are still issued within secure processes.
Certificate is delivered
Once the approval is complete, InTune will submit a certificate request to IdExchange where this request and device will be inspected to ensure all the issuance rules have been met. Next, the request is sent to the certificate authority where the certificate is generated and then to the device.