Easily Issue Smart ID Cards Using Our IdExchange ID Card Security System
IdExchange enables organizations of all sizes to issue and manage smart ID cards to their workforce.
- Achieve immediate compliance with the latest multi-factor authentication regulations
- Consolidate PACS and LACS capabilities into a single card
- Fully customize the way the ID badge looks
- Use self-service issuance models to streamline deployment
- Run in their private cloud to control data security and costs
Issue the ID card type that fits your needs
Numerous configuration options enable you to configure the cards to fit your exact needs
Privileged Access
This ID card has a single digital certificate and is used by system administrators to access sensitive resources.
Workforce ID
This ID card has both logical and physical access capabilities and is used by the workforce for enterprise MFA.
Temporary Badge
This ID card has short lived certificates that automatically expire. Used for visitors or temporary access.
Fed Partner
Used by Government partners, this card is issued using the NIST PIV standard with certificates from a federal bridge CA.
Open doors AND computers with a single ID card
Built in PACS and LACS chips enable the ID Card to serve multiple uses
Use one ID card for both physical and logical access to provide the ultimate in convenience, as well as save money on credential management costs.
One ID Card – Many Uses |
|
|---|---|
| Logical Access | Physical Access |
| Computer Logon | Visual inspection |
| Cloud Authentication | Conference rooms |
| Zero Trust/Passwordless | Server Rooms |
| Message Encryption | Inventory Control |
| Digital Signature | Visitor Identification |
Logical Access Standards
The smart card provides the strongest cryptographic security features and has been formally certified by NIST. Additionally, the smart card uses PIV standards to make it compatible with windows and the most popular certificate authorities.
FEATURES/CERTIFICATES
FIPS 140-2
FIPS 201
PIV/PIV-I/CIV
X.509 certificates via Microsoft, Comodo, IdenTrust
NIST Digital Identity AAL3
Common Criteria EAL 5+
Use the Same Technologies the Largest ID Card Issuers Use
Leverage the best ID card systems in a single, easy to use platform.
Through close partnerships with HID and Suprema ID, the IdExchange ID Card System combines the most powerful ID technology into a single, simple to purchase platform that organizations can use to issue ID cards fast.
| Product | Benefit |
|---|---|
| CyberArmed IdExchange | Identity Proofing, biometric management, chain of Trust, reporting |
| HID Credential Management System | Credential programming, Card Security, PKI management |
| Suprema Biometrics | Fingerprint capture and verification |
| HID Fargo Printer | Credential printing |
| HID Crescendo Smart Card | Smart Card for PACS and LACS |
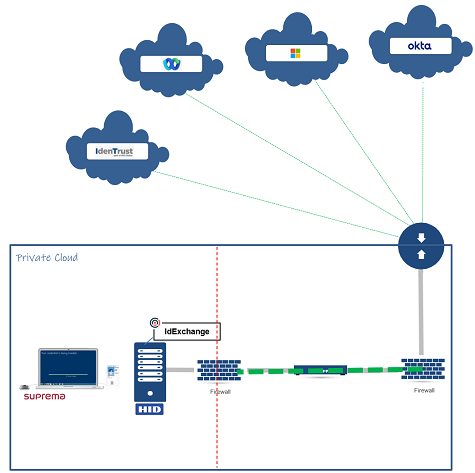
A private, but cloud friendly, platform
Maintain full control of your ID Card System while using your favorite cloud identity provider
Although the IdExchange ID Card Security System is installed and operated in an organization’s private cloud, IdExchange has connectors to make it easy to use the largest identity service providers to extend the use of the ID card for custom programming and enterprise authentication needs.
- Use an ID Card with the Okta Cloud for Enterprise Authentication
- Connect to Azure AD to retrieve identity data for ID card creation
- Leverage a cloud-based certificate authority for Federal Bridge Certificates
- Use the WebEx API for real time remote identity proofing