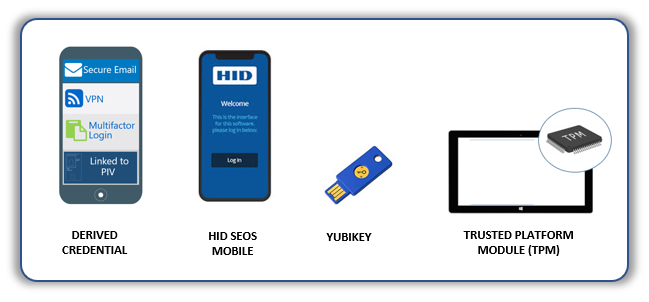
Derived Credential Issuance Aligned with NIST 800-157 and NIST 800-79
Security Management and Data Protection
End to end Encryption: Data at rest and in transit is encrypted using the strongest cryptographic ciphers and require mutually authenticated sessions for all system interactions. Hardware security module (HSM) is supported for additional controls.
Privacy Notifications: Privacy notification screens can be customized to meet organization messaging needs to ensure the appropriate privacy notification is seen and accepted by the system users.
Auditing: All identity proofing and credentialing lifecycle events are tracked and made available through a wide array of pre-designed reports. For custom auditing needs, the auditing API is available as well as a configuration guide to link an external security information and event management system.
Record Expungement: All traces of subscriber information are removed when an authorized official offboards a subscriber. When the subscriber is to be removed, the system deletes all the user’s information and internal data security keys to completely remove all subscriber data from the system.
Infrastructure
Issue different types of derived credentials: Utilize the NIST 800-157 identity proofing workflow to easily issue different types of derived credentials from different credentialing providers. Easily configure a PIV Derived certificate authority to be used in the issuance of hardware based derived credentials.
Automate Revocation and Employment status checking: Automatically check the subscriber’s primary credential status and then revoke their associated derived credentials if the primary credential has been revoked.
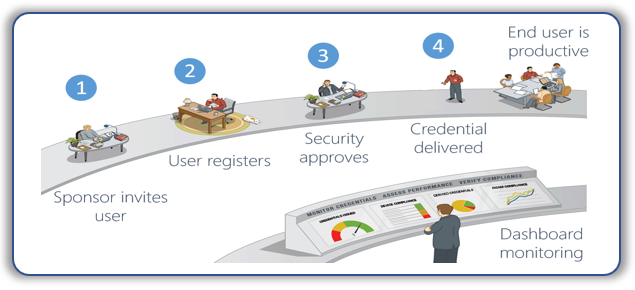
Issuance and Maintenance Processes
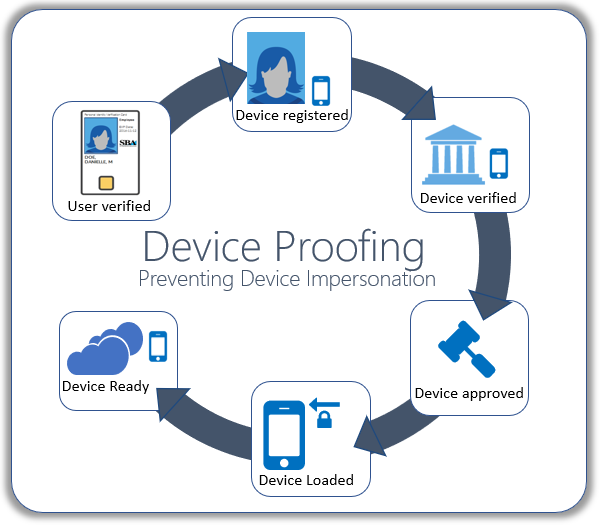
Easily onboard Subscriber verification: The system can securely register any PIV credential using standard protocols to enable the subscriber to login and verify their identity in accordance with NIST 800-147.
Chain of Trust: Easily register and verify different mobile devices, hardware keys, or other derived credential security containers using Mobile Device Management systems, API, or manual data input.
Termination Flow: Synchronize all credential statuses for a subscriber by automatically terminating derived credential if the primary credential is terminated.
Name change: Securely refresh derived credential information when subscriber’s primary credential information changes.