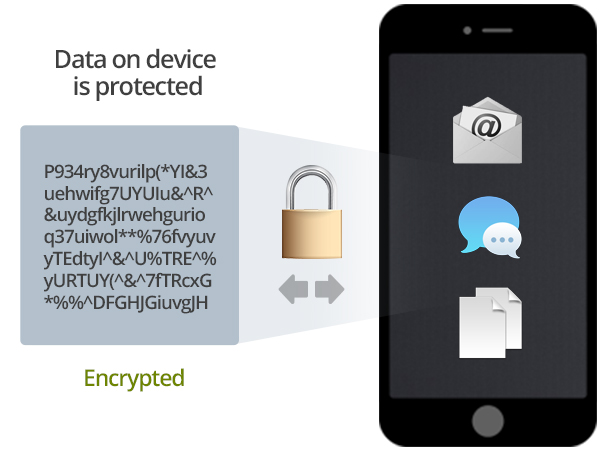
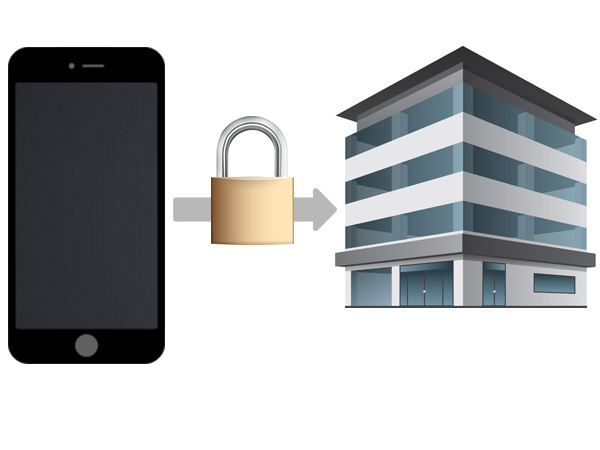
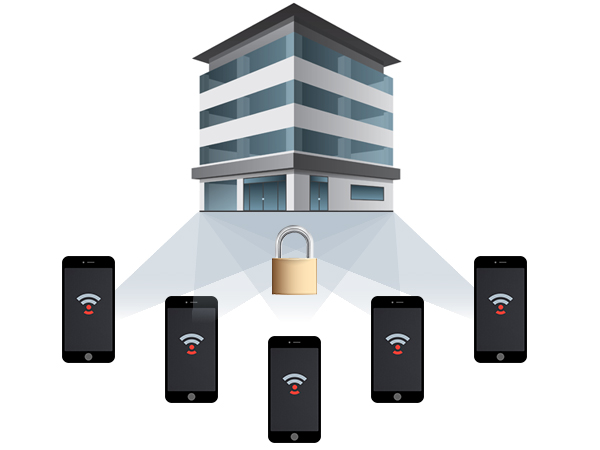
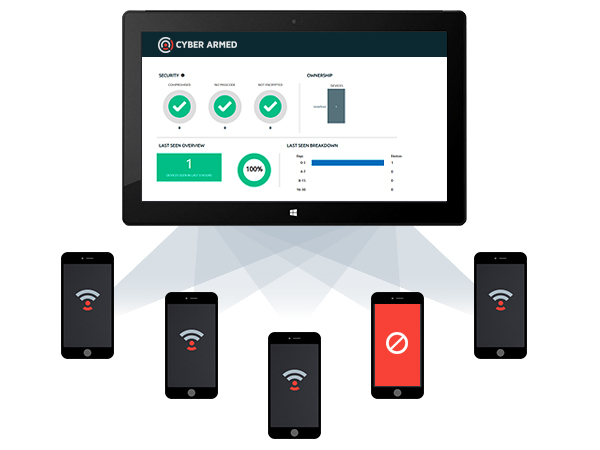
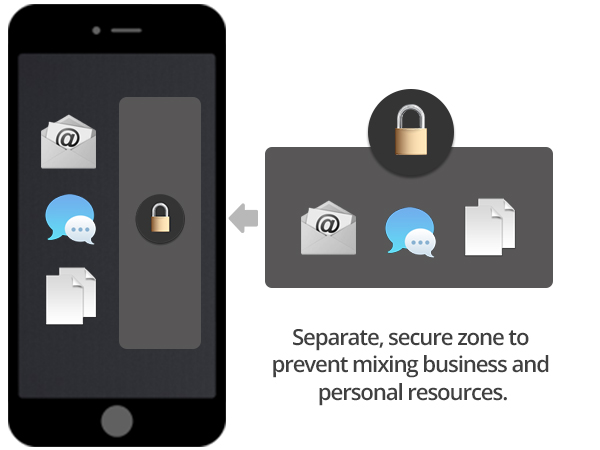
Providing truly seamless Mobile Security solutions.
By providing a combination of assessment and technology integration services, we allow enterprises to quickly secure the mobile devices in their workforce. Furthermore, we work closely with our clients to understand their business needs in order to apply the proper mobile security controls while ensuring productivity and privacy.