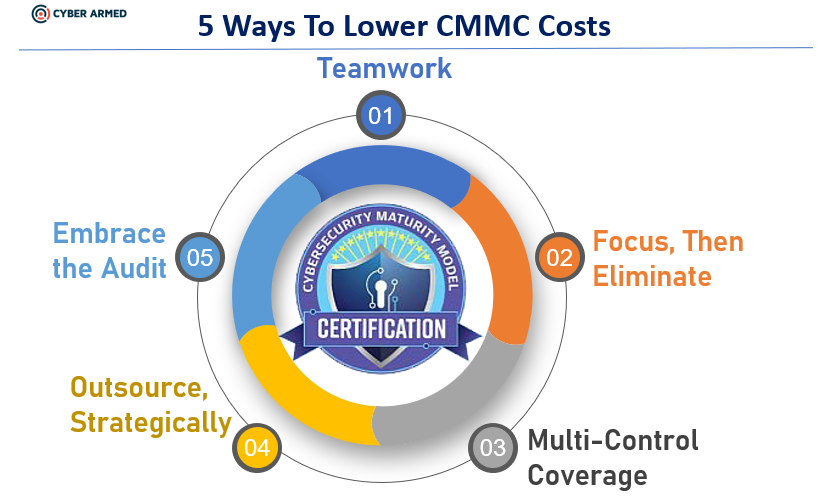
With proper planning and knowledge of practical security techniques, you can drastically lower the cost of achieving your Cybersecurity Maturity Model Certification (CMMC). This blog helps you strategically eliminate risks and turn your focus to implementing the security controls that can cover multiple CMMC security controls at once.
Get your team onboard
The first thing is to ensure everyone in the organization is aligned with the CMMC mission. Any apprehension or pushback will ultimately be more expensive and take longer to achieve CMMC. Be clear to explain that your cyber resources are under attack. It does not matter how large or small your business is, if your company has any kind of computing equipment and performs any kind of task for the DOD, adversaries are actively attacking in order to either obtain access to a DOD network or diminish the capability of DOD.
Make it clear that DOD created CMMC to help protect suppliers and they are extremely serious about companies achieving CMMC to even be considered for DOD contracts. For example:
- There is no CMMC self-assessment. You must be certified by an independent auditor.
- No matter the size of your business, you will need CMMC.
- The CMMC level you need will be specified on a per contract basis.
To be successful, it is critical to get everyone working towards the same goal to avoid costly mistakes. It is imperative the organization does everything possible to help employees understand the threat and why CMMC is a must. The links below provide more detail.
| CMMC Model | The DOD published CMMC with all of the controls and levels. |
| CMMC Overview video | Great video that provides an overview and objectives of CMMC. |
| CMMC Resources by Model and Domain | Great site that allows you to see the controls by phase and provide even more resources by control. It is so helpful because within each control, they provide links to other free resources to help you. |
Focus, Then Eliminate Needless Risk
Given that the costs of CMMC will vary by the complexity of the organization being certified, the level of security currently in place, and the approach the organization desires to implement, there are still numerous areas where the proper learning and preparation can drastically lower costs.
Determine your desired CMMC Level
Strategically plan what level you want to be at to be positioned for your contracts. Given L1 and L2 are just basic controls that you should be using anyway, the baseline for most businesses would be L3. L4 begins to require much more infrastructure and personnel. L5 requires even more advanced automation and correlation. By understanding the proper level for your organization, you can plan your investment properly.
Make it easy to document
Develop a actionable plan to document your efforts. It is critical that your team (and even yourself) be able to have a location to document your plan and progress. When you go through your CMMC certification process, the auditors will want to see all the documents related to your security efforts. Also, you want to make it easy for you and your team to author and update the documents.
*Many organizations do not document properly and it ends up costing them time and money because the auditor could not easily assess the hard work that was performed.
Organize CMMC
The CMMC spans 17 different control domains. in many documents, the domains are always listed alphabetically. However, to provide more structure, the 17 controls should be grouped and organized into a sequence that can be used as a project plan. For example, the sequence below allows us to group the controls into phases.
| Plan | These domains have control objectives surrounding management, awareness, and organizational capability required to implement security. These should be focused on first to help you understand what is required and what you will need to achieve your desired level. |
| Design | This single domain is focused on inventorying your infrastructure. This can help you identify the technical components of your infrastructure and plan the solution approach for each of the technical controls. |
| Implement: | These domains focus on the technical implementation of the security techniques in order to achieve a required security control. These domains will help guide how you implement your controls. |
| Monitor: | These domains are focused on the monitoring and improvement of security controls after they have been implemented. |
| Restoration: | This domain helps to ensure you have proper planning and procedures across the entire organization so that your infrastructure can be restored after a disaster occurs. |
Keys to the Kingdom
Start with a focus on the most important elements of your business. Document your 5 biggest assets that if you were to lose, your business would stop functioning. This focus will allow you to determine what are the critical systems that must be protected.
Infrastructure Pruning
Every business experiences technology sprawl to some extent. Maybe your development team spins up R&D servers and forgets about them or maybe you added some ports to the firewall that were only to be temporary, or maybe you had a few visitors or partners that you granted network access to and forgot about. These innocent actions can be devastating to your company if not addressed.
This is the time to start removing anything not critical to your business operations in order to eliminate the vulnerability and just as importantly, avoid the cost required to document and protect it. Common areas to start analyzing for removal:
- Test servers
- Old Accounts
- Peripherals
- Unrecognized Ports/IP Addresses
Multi-Control Coverage
It is important to realize that the CMMC controls are founded on fundamental security objectives that should already be in place. The CMMC is not prescribing any drastically new technology or solution. Therefore, many organizations already have almost all of the technologies they will need through their existing operating systems, cloud service providers and networking infrastructure. They just need to know how to strategically deploy and augment them to achieve CMMC at the lowest cost.
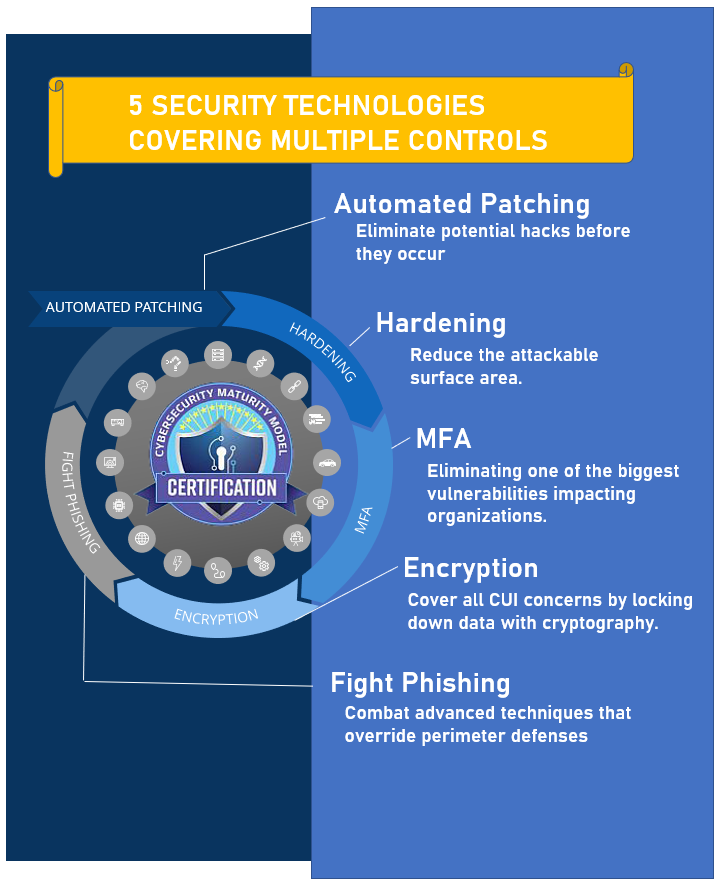
A critical cost saver approach will be to use security techniques capable of covering multiple controls at once. For example, a hardware MFA solution can be applied to 11 CMMC domains and strong encryption can protect any data classification. When securing your infrastructure, it is important to realize that a few sound security techniques can accomplish a tremendous amount.
Automated Patching: One of the most overlooked and powerful forms of cyber defense is ensuring your systems are automatically patched. Many organizations do not turn on auto patching because they are concerned a change may disrupt their infrastructure. Instead, the mindset should be that it is better to have your system disruption because of a patch instead having a hacker exploit it.
Hardening: Many organizations are vulnerable to hackers because they overlooked simple security configurations. For example, they run needless services, permit excessive IP addresses and ports, or grant too much access by default. To help lock down systems, NIST provides free security checklists for almost every conceivable platform. These checklists are compatible with the Security Content Automation Protocol (SCAP) to allow for automation. Visit this site immediately and review the checklists that are applicable to your environment. Next, analyze your systems for compliance and then make any required configuration to ensure the recommended action is taken.
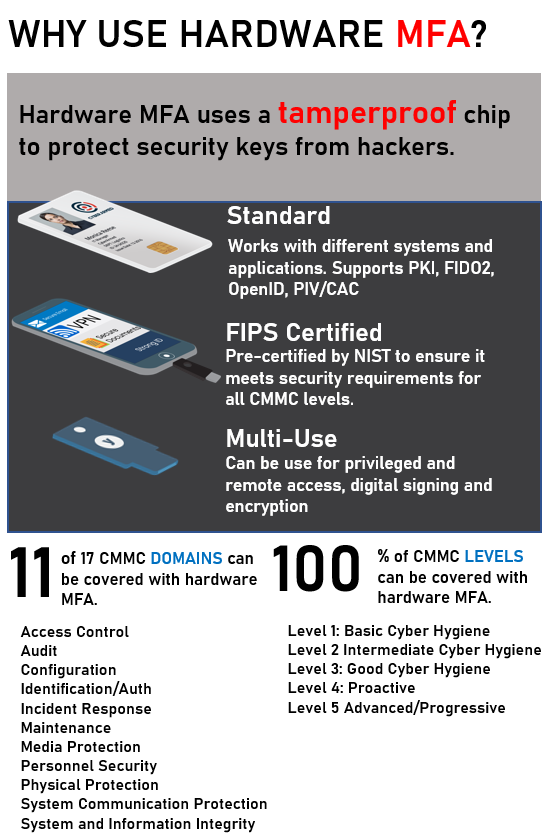
Multi-factor Authentication: MFA is another tremendously powerful technique that drastically adds security and spans multiple CMMC control domains. DOD (CAC), civilian agencies (PIV) and even commercial entities (PIV-C/FIDO2) have embraced MFA and has made it much easier to deploy. When hardware MFA is used, even more encryption and anti-phishing capabilities can be implemented to cover even more control domains. For example, using a FIPS based MFA solution can cover 80% of controls and is used in Level 5 whereas simple password management only achieves 2% of controls and can get you only to Level 2.
Encryption: Another technique that accomplishes multiple objectives is encryption. Not is data properly protected, it also allows you to save time in DOD data classification by just applying strong cryptography by default to all of your DOD related data. For example, you employ disk encryption with a strong cipher and properly managed keys, you have protected your data by default. In the links below, you can begin to cover broad encryption:
Fight Phishing: Even with all the security controls in place, phishing remains one of the most effective attack vectors for adversaries. It is also one of the most devastating to organizations and it will render all of your defenses useless. Phishing is so hard to combat because it preys on the psychology and social needs of humans. For example, adversaries can research your social media, digital identity and other factors that help them better understand how to craft the perfect email to get you to respond. Continuously educate your employees on how to protect themselves and configure servers to provide addition controls. We have provided resources below:
General Phishing Prevention Tips
Microsoft Phishing Training Video
Strategic Outsourcing
A Managed Security Service Provider (MSSP) can be of vital assistance to help achieve CMMC and may even make the most business sense for some organizations. However, you must still invest time in understanding CMMC, your infrastructure and security needs in order to control your costs and ensure you get the best value. If MSSP is for your organization, consider the three purchasing models:
Add-On: Many cloud providers already have CMMC initiatives [ AWS CMMC, Microsoft CMMC] and processes. If you already hosting infrastructure with them, you may be able to add CMMC services to your existing services.
A la Carte: In cases where you need specific security services, you can outsource certain functions to a MSSP. For example, you can outsource specific security functions. For example, maybe you just need and incident response team to achieve level 5 or you need data protection services for data being traded between partners, you can contract to get specific needs covered.
Fully outsourced: If you prefer to fully outsource, you can still reduce costs by fully understanding what is required by CMMC and how your MSSP can provide it cost effectively. Inquire about the specific CMMC capabilities your MSSP provides. Some providers have specific CMMC practices that help ensure you get the services you required.
Embrace the Audit
At the time of publishing this blog, the assessment process is still being determined. However, there are things you can do now to ensure your audit is streamlined to help lower the costs as much as possible:
- Communicate to your team: Set up an audit response team where there is someone responsible for making sure the auditor has everything required to perform their job. Next, ensure your teams are ready to work with the audit lead to ensure they are able to ensure the auditor has all the data and access they need to perform their job.
- Create a Rules of Engagement Audit Practice Statement: While you will be welcoming to your assessment official, make it clear that you want them to ensure they keep all of your documentation and business insight confidential and secure. If possible, create a separate workstation for them to use so they only use your computing equipment and do not use theirs. Ensure that the assessment official uses cryptography to secure your information.
- Make documentation easy to locate: As mentioned earlier, make it easy for your assessment official to obtain the documentation they require. Give them a MFA credential and read-only access to your documentation platform so they can easily browse the documentation.
- Be ready for change: If the assessment official has a finding, be ready to immediately schedule a change request so you can update your infrastructure. Work closely with the assessment official to understand what is required to close the finding. Do everything to close the finding before the assessment official leaves or as soon as you can.
Recap
Please do not be intimidated by the CMMC and remember CMMC is designed to help your business fight the evolving security threats. The CMMC is a critical step in protecting the critical DOD supply chain and DOD WANTS you to be successful. Also realize that CMMC costs can be managed with a few fundamental practices. Use the resources we have provided to get started. if you ever feel overwhelmed or have questions, just send us an email info@cyberarmed.com. Good luck and keep secure!