Isn’t Hardware MFA difficult to deploy?
Traditional hardware MFA distribution models depended on labor-intensive tasks and processes that were expensive to operate and maintain. Often, these processes were not integrated into the organization’s enterprise identity workflows, creating inefficiencies and errors which ultimately made organizations feel that hardware MFA was just too difficult to deploy.
Hardware security keys are quickly becoming a requirement to meet stricter regulations. Even Amazon Web Services is advocating for this technology, giving security keys free to their largest customers. Until now, there were unique logistic challenges associated with securely distributing and programming physical devices for a large, geographically dispersed workforce.
Recognizing the importance of hardware MFA, manufacturers and standards organizations (NIST) have worked tirelessly to create ways to eliminate implementation barriers to make this technology more accessible to organizations of all sizes.
Automation is the Key
In just the past few months, new technologies have emerged that make it extremely simple and secure for organizations to automate the hardware MFA distribution process.
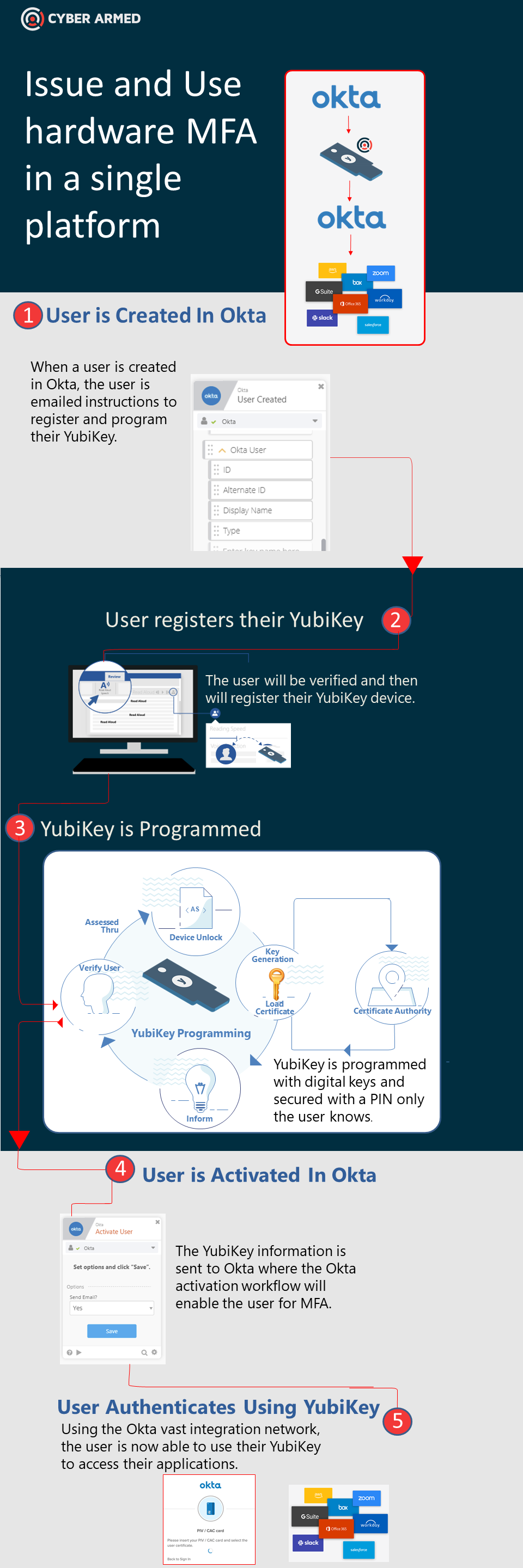
Now secure processes can be implemented that automate the hardware distribution processes as part of the organization’s onboarding process. For example, when a user is onboarded, automated processes will mail the user a security key, help them program the key with a custom PIN and a set of digital keys, and then provision the credentials so the user can immediately use their hardware key to access their applications. Finally, when the employee leaves the company, the offboarding process will automatically revoke the hardware MFA device.
Benefits
- Replace tedious, manual steps with fully automated workflows that are integrated into organization onboarding and offboarding processes
- Automatically mail and track a hardware security key to a remote workforce member
- Use self service processes to give the workforce member the ability to program their hardware security key
- Leverage notification events to automatically enable applications to use hardware MFA
Architecture
Central to the architecture is the Okta Identity platform. Okta is unique because 1) their platform can immediately enable any application they support to use a hardware security key for authentication, and 2) the platform enables you to create custom workflows that can be used to automated the issuance of hardware MFA programming.
For the hardware MFA programming, the IdExchange platform is used because it provides device programming APIs for Okta to call. Additionally, it has simple to use self-service dashboards to guide the user through the programming processes and uses secure device programming model for secure remote personalization.
Finally, we will use the YubiKey FIPS hardware device because it is certified by NIST, works great with mobile devices, and supports a multitude of authentication options including PIV and FIDO2.
How it works
To connect the systems, we will use the Okta Advanced workflows where we can place the hardware MFA programming process into the user onboarding process.
Demonstration
The video below demonstrates the Okta workflows working with IdExchange to help a user program their YubiKey device.
Conclusion
Hardware MFA issuance can be made much easier with the proper technologies. The Okta workflow can automate the process to make sure everyone in your workforce is able to use hardware MFA to access their applications.