How Secure Channel Protocol Improves MFA Management
Secure Channel Protocol (SCP) provides an ultra-secure way to encode hardware based MFA devices such as smart cards, hardware security modules, and USB keys. Once reserved to specialized products, SCP has now become mainstream with the latest YubiKey FIPS SCP device.
This blog provides an overview of the security features of Secure Channel Protocol (SCP) and more importantly, how these features help improve MFA management through more efficient issuance models. For greater technical detail coverage of SCP, visit Global Platform and the YubiKey 5 Series technical manual. If you want want to look at source code and APDUs (please think about joining our dev team!) the visit the Global Platform Pro repo.
SCP Overview
SCP controls the way the programming interface of a hardware device can be accessed. For example, if you want to load a certificate or unlock a YubiKey device, a mutually authenticated connection via SCP must be established in order to perform these actions. What makes SCP unique and secure, is the process of authentication and the way the keys are protected. Let’s take a closer look at these SCP features and why they matter.
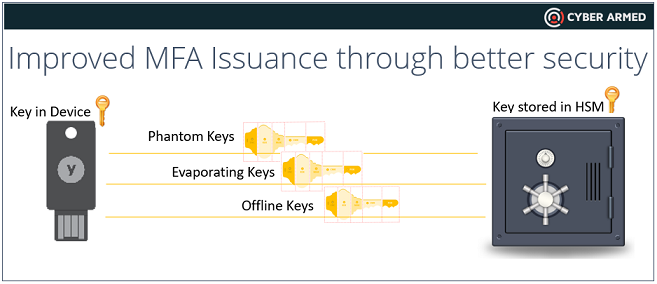
Phantom Keys: Unlike traditional device authentication systems where the management key is sent directly to the device (similar to how a password is used when authenticating), SCP authentication keys are never sent directly to the YubiKey. Instead, you send a value encrypted with the authentication keys to the YubiKey which then performs the validation. The advantage of this approach is clear…since you never send the management key directly to the device, it cannot be intercepted and is never in a position to be stolen by malware or some other attack vector.
Evaporating Keys: Another protection device is the use of per-session keys that are automatically destroyed after each transaction. Each time the terminal interacts with the YubiKey during an encoding operation, single-use secure session keys are generated that must be used for all instructions sent and received by the device. Once the session is over, the keys are never usable again. This is powerful because even if malware captures the session keys, the malware cannot later use the keys to establish a new connection with the YubiKey.
Encryption from server to device: When using SCP, every byte that is sent to and from the device from the terminal software is encrypted. When combined with SSL and other security transport mechanisms, every byte from the server all the way to the device is protected, preventing eavesdropping at all levels.
Learn more ways SCP can help improve your credentialing capabilities.
Subscribe to our email list to get unique tips, exclusive research, how to videos, and advanced configurations to help you continuously improve your MFA capability.
Keep Learning
Using security to lower operational costs
With the security enhancements provided by SCP, organizations have many more secure options to deploy and manage YubiKey devices. Before SCP, it was recommended that device programming be performed on a closed network to prevent eavesdropping, typically in the corporate badging office. However, with SCP protecting the keys and encrypting traffic end to end, organizations can enable remote programming using self service wizards. Let’s take a look at two scenarios: 1) Remote issuance, 2) Remote maintenance
Remote issuance: In this use case, your workforce participant can securely encode their YubiKey in a remote location. It would work like this:
- Person receives their YubiKey
- Person logs into web portal where both their identity and YubiKey is verified
- Yubikey generates and sends random value to the programming server
- Programming server uses the hardware security module to encrypt the random value with the management key and sends it back to YubiKey for validation.
- The YubiKey and server now have a private session where encoding instructions are communicated.
- YubiKey encoding is completed and ready to use
Remote maintenance: Now when your end users lock their device, they can call into a help desk and get a temporary card to unlock their device. They no longer have to visit a credentialing office.
Putting SCP to work in your organization
SCP is a powerful security tool for configuring hardware MFA devices and can help drastically reduce costs when properly implemented. We have fully embraced SCP in our IdExchange server to allow us to securely achieve remote and offline programming of YubiKey devices. If you have questions about how SCP can help your credential issuance program, send us an email at support@cyberarmed.com.