How To Add Virtual Smart Cards To Your PIV-C Issuance Process
Now that enterprises have become comfortable with cryptographically secured hardware provided by PIV-C, they are looking for ways to add convenience and agility to their mobile device landscape while maintaining the same level of security controls that the PIV card provides…but without the physical card or reader. In this blog, we describe how to create a Virtual Smart Card issuance capability with all the enterprise level management and usability features required for a scalable operation.
Agenda
This blog will help you learn how to issue Virtual Smart Cards for your enterprise workforce. It describes:
- What a Virtual Smart Card Is
- Security Benefits
- Architecture
- Implementation Steps
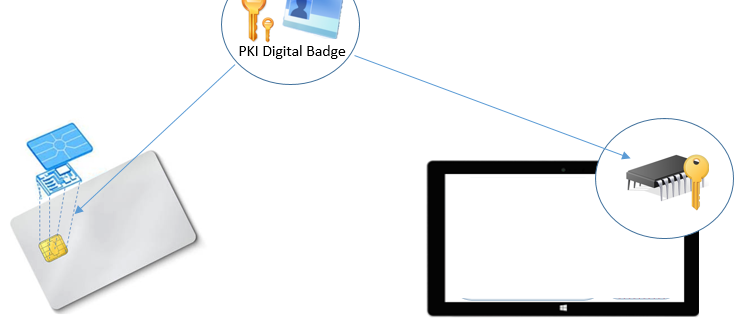
What is a Virtual Smart Card (VSC)?
A virtual smart card is stored in a secured chip known as a Trusted Platform Module (TPM). This TPM provides the same security features as a PIV smart card, but the chip is on the device’s motherboard, not embedded in an ID Card. From a convenience point of view, this design is spectacular because the user can achieve the same tamperproof security controls provided by a PIV Card even if their device lacks a smart card reader. With this approach, enterprises can easily extend cryptographic multi-factor authentication features to their mobile assets to complement their PIV Card issuance capabilities.

VSC Security Features
Conceptually, the VSC is similar to taking the chip from your PIV card and permanently storing it in your mobile device. While the VSC is different from your actual PIV card, it provides the same core security features that make the PIV card so effective. This matrix provides a side by side comparison of the two.
Hardware-based security (Non-exportability)
One of the best (if not the best) security features of the VSC is that the keys cannot ever be exported. The reason this is important is that if the device is ever stolen or is impacted by malware, the keys cannot be extracted and used by an unauthorized user. This provides extraordinary protection to ensure that the user’s keys can never be compromised if a hacker steals the device or clones the hard disk.
Anti-Hammering
Another benefit of using the hardware approach to storing keys is the way the hardware can protect itself against traditional brute force attacks. Using a process known as anti-hammering, the chip will be able to detect fraudulent access attempts and will lock itself using an advanced algorithm to make sure an attacker cannot gain access to the TPM, but it does not permanently lock out a valid user that accidentally entered the PIN incorrectly. This Microsoft link has a great technical explanation of the anti-hammering feature.
Multi-Factor Compatibility
The VSC provides immediate MFA security features out of the box with no additional hardware or software. For enterprises that have invested in cryptographic/PKI based authentication protocols, now their mobile devices can also utilize this trust fabric faster and easier.
Business Benefits
The cost and usability nature of VSC can enable enterprises to deploy hardware-based cryptographic tokens to their workforce at scale.
Convenient
While I do love traditional PIV Cards, I will be the first to admit that they can be challenging to use when I am on my mobile device. Like everyone else, when I am on the go, I just want to be able to use my PKI credentials immediately without anything getting in the way. With the VSC feature, I now always have secure access to my credentials to protect my data and logins. For enterprises, this convenience is critical as it allows IT to implement the highest cryptographic security controls without disrupting the productivity of their workforce.
Cost effective
Modern devices (even desktops) are being delivered with VSC capabilities built-in out of the box. There is no need to purchase separate hardware for credential storage. Additionally, the virtual smart card behaves like a traditional PIV card so there is no need to buy additional software to use its multi-factor authentication and data protection security features.
Consolidate
The VSC implements the most secure multi-factor authentication protocols as well as provides the basis for Windows Bitlocker data protection. Since these features are now built into the user’s device, the enterprise can eliminate other proprietary multi-factor authentication products and use the VSC exclusively.
What you will need
If you are like me, you are so excited about the security and usability features of VSC and want to get started immediately with implementation. However, before you jump right in, you will need to prepare your enterprise for some operational changes before full roll out. Additionally, you will want to think about an architecture that is scalable and ready to go for full operations so you do not waste time evaluating a solution that will need to be reworked to meet enterprise needs.
Updated Backup/Disaster Recovery Procedures
Due to the strength of TPM security controls, TPM technologies can have a dramatic impact on the way an organization manages the recovery of their IT assets. Once the TPM is turned on and configured, traditional data backup and IT management processes no longer work without also taking great care in backing up the TPM information. The reason is, the TPM implements hardware-based security that effectively makes the data unexportable to any other device without proper security controls. Personally, I love this feature because if I lose my laptop, someone cannot just take out the hard drive and copy it. However, it does mean enterprises must take great care in securely backing TPM information to effectively provide a secure recovery process for their workforce. Microsoft provides guidance here.
Updated subscriber agreement
The virtual smart card implements the same security features as the traditional PIV card…but without the PIV card and reader. Sometimes, the end user does not even realize they are using an advanced crypto device. However, they should still be informed of their PKI responsibilities to protect their keys. Therefore, do not forget to include the subscriber agreement in the VSC issuance process.
Scalable architecture
Most of the VSC implementation guidance available describes a simple architecture comprised of 1 laptop and a test certificate authority. While this guidance is spectacular for learning how VSC works and even for evaluation purposes, an enterprise must consider what it takes to issue and manage 1000s of VSC credentials. The reason for this is because once security managers and users start using VSC technology its use will only become more popular in the enterprise. The following are elements that must be factored into the architecture to ensure a successful transition into full operations:
- Initialization – how will the VSC be initialized and managed
- Post issuance – how do you update, suspend or terminate a certificate
- Credential Linkage – given users typically have multiple credentials, how can the VSC be linked to a user’s current credential list
- Certificate Trust – How will the certificates be used and trusted
Technologies Required
In the guidance below, we will be issuing virtual smart cards using a high speed, scalable architecture that can support PIV-C and PIV-I derived credentials. Note, this architecture is for enterprises ready for full VSC deployment. If your enterprise is still in the early phases of research, I recommend this great Microsoft tutorial to get started.
TPM Chip
The great thing is that Microsoft is requiring TPM technology to part of the hardware stack for Windows 10. For an enterprise, this means you will already have the TPM in your infrastructure without additional costs.

VSC Management Platform
The management platform will provide centralized management for all of the VSC credentials issued within the enterprise. This platform will also enable administrators to easily manage the certificates at an enterprise level. The HID CMS product provides the features for enterprise VSC management along with advanced APIs for linking issuance and post issuance activities to automate the management of VSC credentials.
Certificate Authority
The CA will provide the certificate services for the VSC. In this example, we are using a cloud-based, managed certificate authority from IdenTrust. IdenTrust provides an entire spectrum of certificate options and has the core industry certifications that can allow for immediate scale and trust for immediate scale and trust for PIV-I and Direct Trusted Agent.
VSC Issuance Software
The issuance software walks the user step by step through the process of encoding their VSC and drastically streamlines the traditional virtual smart card issuance process and automates manual steps for initializing the VSC. Additionally, the issuance software provides the necessary authentication services to ensure the user has permissions to encode their VSC.
Implementation Steps
1) Configure CMS to issue Virtual Smart Cards
In the CMS Customization/Devices console, check the option for Virtual Smart Cards.

2) Connect the CMS to the Certificate Authority
Add a New Certificate Authority

3) Create the device policy
Now that the CMS has been configured for VSC and for the certificate authority, the next step is to configure the device policy. The device policy is what allows the enterprise to issue VSCs at scale as this feature allows the admin to set the PIN protection and certificate details at a global level.
4) Encode the VSC


Conclusion
Virtual Smart Cards give enterprises another extremely useful way to equip their workforce with strong authentication and data protection tools. Similar to the PIV Card, the VSC can provide unparalleled security to withstand the latest cyber threats. If you have more questions about the architecture or want to see a demonstration, please send us an email to sales@cyberarmed.com.



Leave a Reply
Want to join the discussion?Feel free to contribute!