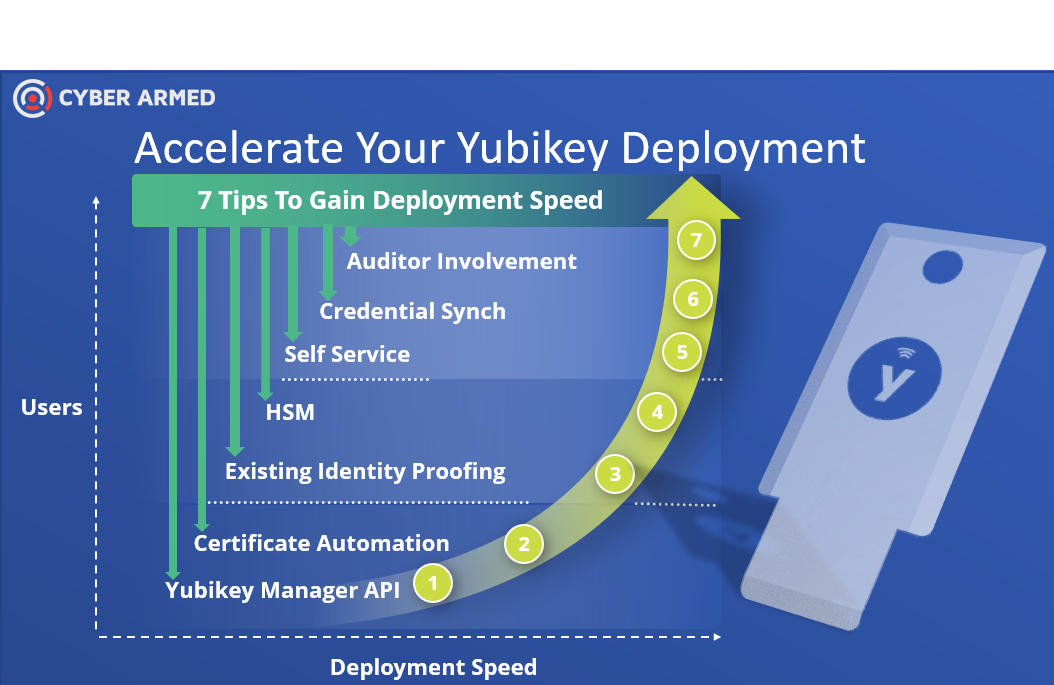
Give Yubikey devices to users faster with these 7 tips to accelerate your Yubikey deployment! If you have started the enterprise roll out of Yubikey devices and now want more deployment speed to reach more people faster, do not worry – we have you covered. The following 7 tips provide techniques on how IT managers and architects can increase capacity to deploy and manage Yubikey devices faster while simultaneously enforcing strong security controls.
Yubikey Success
Given the extensive security capabilities and ultra-usable design of the Yubikey, organizations started to pilot Yubikey devices within their infrastructure as fast as they could. They quickly obtained a Yubikey, manually configured it, and handed it to a few people for testing. Things went so well with testing, IT managers had immediate requests to deploy the Yubikey devices enterprise wide…. immediately!
Capabilities for Achieving Greater Deployment Speed
With the Yubikey guides and utilities, a Yubikey is very easy to configure. The designers spent a lot of time to make it easy for a typical consumer to obtain a Yubikey and put it to work. However, when transitioning to a large-scale rollout where speed and capacity is required, organizations also need additional; automation, task delegation, and reporting capabilities. Let’s briefly explore these elements below:
- Certificate Delivery: Deploying multiple Yubikey devices at one time requires advanced certificate authority interface design. Automated processes must be in place to ensure the Yubikey device is known to the organization and has been verified for certificate issuance.
- Key Derivation: When issuing large sets of Yubikey devices, if the management key is not properly generated and is discovered from 1 Yubikey device, all of the Yubikey devices are at risk. Therefore, the Yubikey management key must be different for each Yubikey device. This requires a strong process as well as a technical capability to generate secure values and provide secure storage so the key is not discoverable.
- Report Distribution: As more Yubikey devices are deployed, more reporting and instrumentation is required because tracking device history, certificate distribution, chain of custody, etc., is needed to ensure the issuance processes are secure. Additionally, auditors will need their own reporting access to ensure they are able to efficiently perform their duties without requiring IT support.
- Automatic Credential Registration [for example, Linking Duo Security Account to Yubikey OTP]: Many organizations will manually register their Yubikey with Duo Security, not understanding there is an API for this process. When deploying at scale, both the Yubikey API and the external credential provider’s API (in this example Duo) should be integrated to automate this configuration process.
How to Accelerate Your Yubikey Deployment
The following techniques will help you build additional capabilities while also covering architecture elements that provide additional capacity. The ultimate goal of these tips is to help you get Yubikey devices deployed as fast as possible. We hope they save you time and accelerate deployment.
- Harness the Yubikey Manager API: Many organizations use the Yubikey Manager GUI exclusively to configure their Yubikey Devices. However, the Yubikey API is extensive and allows full automation for the most manually intensive tasks. Learning to harness the API enables the automation of; credential consolidation, secure key management change, and enterprise device tracking.
- Use certificate automation: When in a test phase, certificates are loaded manually with the Yubikey Manager Utility. This process requires a manual key generation and certificate signing request (CSR) submission process. Instead, at the minimum, organizations should use Yubikey Mini-driver with the Microsoft CA to deliver certificates to the Yubikey Device. Using this configuration is much faster because it eliminates numerous manual steps when compared with the Yubikey Manager.
- Use existing identity proofing: If your organization is already using PIV, CAC, or other smart cards, but desires the Yubikey to add FIDO2/WebAuthnN or link their Duo security token to an AAL3 device, eliminate repetitive identity proofing steps and instead, let the cardholder use their smart card to issue their Yubikey [see demo here].
- Use an HSM to secure the Yubikey: An overlooked, but critical task, is changing the Yubikey default management key. This task is usually manually performed using the Yubikey Manager with a static key that is known. Instead, use the HSM to securely generate a random key to replace the default management key. While it will take longer to learn how to use the HSM, the time saved in the long term is well worth the investment.
- Implement self-service as much as possible: When deployment really begins to ramp up, long lines will develop causing capacity constraints in your issuance process. To prevent this constraint, do everything possible to enable the user to encode their Yubikey via self-service. For example, if basic certificate enrollment is required, set up the Microsoft CA + Yubikey Mini driver to enable the user to enroll their own certificates. If more advanced self-service management is required such as Pin Unlock, remote ID proofing, you should consider a more advance platform (see conclusion).
- Automate credential synch: Utilize the 3rd party API interfaces in coordination with the Yubikey API. For example, if provisioning a Duo Security Yubikey OTP, use the Duo Security API with the Yubikey API to automate the provisioning.
- Involve auditors: One of the most overlooked elements of a Yubikey deployment is the auditing function. When PKI based tokens are involved, there is usually a separate organization that audits the issuance process to ensure the devices have been issued under proper security controls. Additionally, they look for chain of custody to ensure devices have been distributed to the correct owner. It is important that an auditor be satisfied with the reporting capabilities so the Yubikey rollout is not halted because reporting data is not available.
Conclusion
The Yubikey API, utilities, and in-depth technical guides provide everything you need to get the deployment acceleration you need. However, if you need a little assistance, want a full COTS solution, or just want to outsource your entire Yubikey deployment, please email us at support@cyberarmed.com and we would be happy to help. We have the installation methodologies, partnerships and unique tools that will help you roll out your Yubikey devices with speed to allow you to quickly:
- Issue thousands of Yubikey devices at scale
- Automatically integrate Duo Security to instantly create an AAL3 Multi-Credential Yubikey
- Use existing PIV cards for issuing a Yubikey as a derived credential
- Integrating Yubikey distribution into your existing security workflow
Do not hesitate! Give your workforce the strong MFA they need as fast as possible.