Yubikey FIPS + Duo Security = Increased Authentication Capabilities
This article explores how the Yubikey FIPS + Duo Multi-Use Authentication Token can immediately help agencies meet new authentication needs with a secure token that is easy to use and deploy. It covers the motivation for seeking new authentication techniques, how this token meets the most stringent security requirements and finally the uses and benefits of this approach.
Motivation
Although the PIV card is the strongest authentication token that can be used, the PIV card alone fails to meet many of the evolved operational needs of today’s advanced agency infrastructures. These deficiencies can leave large groups of users without credentials or even force certain resources to rely on outdated authentication schemes because they do not support traditional PIV cards. Let’s explore some common problems below:
- Non-PIV Eligible: From short term contractors to public consumers, many users of government computing resources are not eligible for a PIV credential. Instead, agencies must still allow lower assurance mechanisms such as passwords so these users can access the systems they require.
- Cloud Platforms: With agencies increasingly utilizing third parties for computing workloads, they are not always able to control the authentication process and must adopt the authentication controls that are in place. Many times, these controls are not compatible with PIV cards.
- Usability: PIV cards require extensive resources such as readers and middleware to function properly. However, many users may require a token that works by itself without additional hardware or software needs.
To address these shortcomings, NIST and OMB have issued guidance to help agencies augment their authentication approaches. For example, OMB M-19-17 memorandum formally recognizes the need for federal agencies to start adopting the newer authentication technologies required to meet zero-trust security needs associated with cloud computing and mobile first architectures. Specifically, OMB M-19-17 states that “Agencies shall work with the Federal CIO Council, the Federal Privacy Council, and NIST to pilot additional solutions (e.g., different authenticators) that meet the intent of HSPD-12 and advance the technical approach to managing identities.
Selecting the proper authenticator
With so many authentication choices, how can an agency determine the best way forward? Thankfully, NIST has provided guidance in their NIST 800-63 B to narrow down the options. This document provides 3 clear authentication assurance levels (AAL) with the associated required security controls for each respective level. For example, AAL1 has the lowest security and AAL3 has the highest security.
We focused only on authenticators that achieve AAL3 as we wanted to provide a token that could withstand rigorous security audits and meet the broadest authentication needs. Also, based on over a decade of issuing PIV cards, we developed a deployment checklist a token must possess in order to be considered practical for real world deployment scenarios as we wanted to ensure an agency would be able ultimately to deploy these authenticators at scale.
| Deployment Check list | |
| Capable of being issued via NIST Derived Credential Security Process | For any high assurance credential, the agency should ensure it is given to the correct person only after they have been properly verified. |
| FIPS Certified | The token hardware must be certified to the strongest FIPS level so that it is capable of being used with all the agency’s systems. |
| PIV Compatible | The data model must be able to implement PIV in order to allow the authentication token to compliment a PIV credential. |
| OTP | The hardware must support additional schemes in order to provide a range of authentication options. |
| Attestation | The onboard firmware must provide a way to perform attestation of the keys issued on the device. |
| Enables Key Recovery | The hardware must be certified and firmware must support key history so that encryption keys can be recovered securely. |
| Usable | The authentication token must be able to be used out of the box without additional hardware or software. |
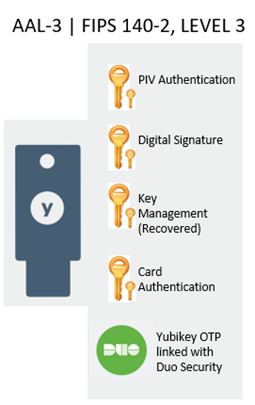
Yubikey FIPS + Duo Security via PIV Derived
The Yubikey FIPS + Duo Security combination achieves AAL3 while also meeting the deployment checklist. This token implements FIPS hardware-based security, OTP, and is easy to use. For example, we could use the on-board PIV certificates for smart card logon, encryption keys to protect messages, and finally use the Duo Security OTP for MFA for cloud applications… all in one FIPS certified device.
| Yubikey FIPS | · FIPS 140-2: NIST Certificate 3517 (Overall Level 2, Physical Security Level 3) · Strong multi-factor authentication · Easy and fast authentication · Crush resistant & waterproof · Multiprotocol support on a single key |
| Duo | MFA for latest cloud platforms
Adaptive authentication Policy enforcement |
| PIV | PIV PKI compatible |
From an authentication strategy point of view, this token immediately solves numerous challenges related to usability, compatibility, and distribution. For example:
- The all in one form factor can be used without additional hardware and fits on a key chain, making it easy to distribute to more users.
- The onboard cryptography features are PIV compatible to work with existing PKI investments. Further, key recovery is supported so that an existing PIV card holder can utilize this token for encryption activities.
- The onboard OTP functionality is fully integrated with Duo Security to accelerate MFA for the newest platforms.
- The hardware is FIPS certified at the highest level insuring its approved use for even the most secure authentication scenarios.
Authentication Functionality
The biggest benefit to this approach is the dramatic increase in authentication coverage provided by the Duo and Yubikey integrations. Not only does this token support PIV (so it behaves exactly like a PIV Credential), it also integrates the OTP/MFA functionally from Duo security as well as all of the integrations from Yubikey. The links below provide links to the current integrations.
PIV: Smart card logon, SSL, Encryption (supports recovery), Digital Signature
Issuance Model
Distribution of the token has also been designed to address the unique challenges faced by agencies that are augmenting their authentication capabilities. The issuance model has been designed to work with the agency’s existing PKI and enrollment processes to support all users regardless of whether or not they had an existing PIV card. The system supports both the NIST PIV derived credential (for existing PIV card holders) and remote identity proofing (for non-Piv eligible users).
Users with a PIV Card: Users with an existing PIV card will use the NIST PIV Derived Credential issuance model to obtain their Yubikey + Duo Token.
- User logs in with their PIV Credential
- The user inserts their Yubikey FIPS Device
- Yubikey is secured (management key and pin unlock key are changed from default to an unknown value)
- IdExchange routes the request to the certificate authority and Duo security server for necessary registration and credential issuance.
- The certificates are loaded onto the Yubikey
Users without a PIV Card: Non-PIV eligible users will use a streamlined a remote issuance to obtain their Yubikey + Duo Token.
- User applies for a credential online
- Agency reviews the request, if permitted, approves the request.
- User is enrollment and verified by the agency (in person or remote)
- IdExchange routes the request to the certificate authority and Duo security server for necessary registration and credential issuance.
- The certificates are loaded onto the Yubikey FIPS Device
Next Steps
The Yubikey + Duo token can immediately advance an agency’s authentication capabilities by ensuring authentication is easier to use by everyone that needs access to their resources. It allows for adoption of new authentication mechanisms while still using the most secure FIPS hardware. To see a demonstration of the issuance process, please visit our virtual demo. If would you like to test this capability in your agency, please email us at sales@cyberarmed.com or reach out to your Yubikey or Duo Security representative.

 @CyberArmed
@CyberArmed